authentication protocol | ntlm | kerberos
Published 5 years ago • 5K plays • Length 11:45Download video MP4
Download video MP3
Similar videos
-
 2:49
2:49
ntlm | windows authentication
-
 5:25
5:25
kerberos - authentication protocol
-
 2:19
2:19
how kerberos works
-
 3:52
3:52
kerberos and microsoft ntlm
-
 6:08
6:08
kerberos - authentication protocol
-
 16:52
16:52
kerberos authentication explained | a deep dive
-
 3:32
3:32
windows authentication
-
 4:16
4:16
kerberos simplified - cissp exam prep
-
 6:50
6:50
4.6 - authentication protocols (kerberos, saml, openid, oauth, ldap) (comptia security sy0-701)
-
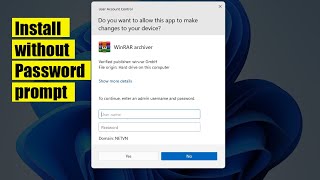 4:59
4:59
how to allow users to install without password in domain
-
 17:30
17:30
cyberark - configure saml authentication for psm for windows
-
 0:42
0:42
how ntlm auth works
-
 3:46
3:46
kerberos vs. ldap: what’s the difference?
-
 15:44
15:44
what is ntlm ? how does ntlm authentication work ? ntlm protocol: pros and cons of this method ?
-
 8:08
8:08
ntlm vs kerberos authentication
-
 4:44
4:44
kerberos to ntlm fallback authentication bypass (ms16-101 / cve-2016-3237)
-
 6:23
6:23
ntlm & kerberos authentication process
-
 32:15
32:15
ntlm & kerberos, how outlook authentication works with exchange and office 365
-
 4:18
4:18
kerberos vs ntlm domain authentication
-
 10:30
10:30
4 2 1 ldap, kerberos, and ntlm