criminal use of computer systems
Published 2 years ago • 2.3K plays • Length 4:20Download video MP4
Download video MP3
Similar videos
-
 14:52
14:52
computer crime and its effects
-
 9:43
9:43
computer crimes: introduction
-
 3:17
3:17
types of computer crime
-
 3:01
3:01
laws on computer crimes
-
 39:49
39:49
criminological theories of computer crime
-
 7:56
7:56
types of computer crimes
-
 18:04
18:04
chapter 3, computer and internet crime, part 2: types of exploits (18:04)
-
 12:50
12:50
types of computer crimes
-
 29:37
29:37
the computer chronicles - ibm clones (1985)
-
 17:54
17:54
phishing attacks are scary easy to do!! (let me show you!) // free security // ep 2
-
 7:57
7:57
wedding - our special day | @amandhattarwal & shradha khapra (@apnacollegeofficial )
-
 18:55
18:55
introduction to cybercrime | types of cyber crime | how to prevent cyber crime | intellipaat
-
 14:13
14:13
computer misuse act
-
 0:48
0:48
types of cyber crimes part i | strongbox it
-
 18:16
18:16
causes of cybercrime and preventive measures
-
 3:14
3:14
what are the different types of computer crime laws
-
 1:54:07
1:54:07
early computer crime
-
 1:03:38
1:03:38
computer crime and criminal law 101 (sha2017)
-
 13:41
13:41
cyber law in a singapore context
-
 28:31
28:31
basics of internet and cyber crimes
-
 14:55
14:55
cyber crime
-
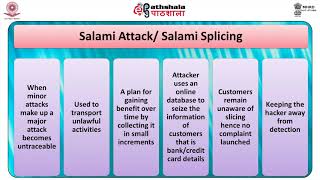 25:09
25:09
m-10. introduction to cyber crimes and their classification