cs387: applied cryptography - promo
Published 12 years ago • 8.4K plays • Length 0:54Download video MP4
Download video MP3
Similar videos
-
 0:54
0:54
applied cryptography course overview
-
 1:25
1:25
summary - applied cryptography
-
 2:31
2:31
provide scarcity - applied cryptography
-
 0:23
0:23
useful certificates - applied cryptography
-
 1:35
1:35
welcome - applied cryptography
-
 1:00
1:00
summary - applied cryptography
-
 1:10:02
1:10:02
lecture 24: man-in-the-middle attack, certificates and pki by christof paar
-
 1:22:01
1:22:01
21. cryptography: hash functions
-
 8:34
8:34
was your vote counted? (feat. homomorphic encryption) - numberphile
-
 1:03
1:03
overview - applied cryptography
-
 3:33
3:33
summary - applied cryptography
-
 1:48
1:48
certificate details - applied cryptography
-
 1:59
1:59
summary - applied cryptography
-
 1:15
1:15
one way function - applied cryptography
-
 0:17
0:17
thwarting dictionary attacks - applied cryptography
-
 0:19
0:19
toy substitution cipher 2 solution - applied cryptography
-
 0:16
0:16
rsa - applied cryptography
-
 2:18
2:18
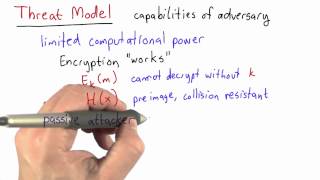
threat model - applied cryptography
-
 0:35
0:35
observing a vote - applied cryptography
-
 1:56
1:56
summary - applied cryptography