cyber threat intelligence explained
Published 6 years ago • 56K plays • Length 2:33Download video MP4
Download video MP3
Similar videos
-
 3:43
3:43
mitre att&ck® framework
-
 1:32:00
1:32:00
mitre tech talks: cyber threat intelligence
-
 4:28
4:28
how mitre att&ck works
-
 34:40
34:40
bringing intelligence into cyber deception with mitre att&ck®
-
 7:53
7:53
mitre att&ck framework for beginners
-
 2:48
2:48
cyber security at mitre
-
 2:25
2:25
using threat intelligence with mitre att&ck
-
 8:56
8:56
what is mitre att&ck | how can use mitre att&ck framework | cyber kill-chain | rajneesh gupta
-
 3:27
3:27
cybersecurity expert demonstrates how hackers easily gain access to sensitive information
-
 16:43
16:43
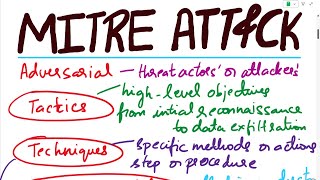
mitre attack | mitre att&ck | mitre att&ck explained with an example | mitre att&ck analysis
-
 13:24
13:24
att&ckers think in graphs – january 2021
-
 28:18
28:18
the mitre att&ck framework explained | threat intelligence and modeling | part 1
-
 25:11
25:11
mitre att&ckcon 2.0: raiders of the mitre framework: how to build your own threat library
-
 4:04
4:04
cyber threat intelligence and mitre | mehzad sahar
-
 11:45
11:45
introduction to att&ck navigator
-
 26:22
26:22
mitre att&ckcon 2.0: using threat intelligence to focus att&ck activities
-
 41:44
41:44
mitre att&ckcon 2018: advancing infosec, keynote presentation
-
 2:41
2:41
mitre att&ck explained with phishing email | cyberres sme submission
-
 53:43
53:43
lecture 06: understanding mitre att&ck: a guide to cyber threat intelligence
-
 6:51
6:51
cybersecurity threat hunting explained
-
 13:39
13:39
mitre att&ckcon 2.0: att&ck updates – tram