f5 awaf managing attack signatures mitigating attacks and threats
Published 3 weeks ago • 14 plays • Length 5:18Download video MP4
Download video MP3
Similar videos
-
 12:57
12:57
f5 awaf - deploy attack signatures | mitigating attacks and threats
-
 10:25
10:25
f5 awaf - creating user-defined attack signatures and attack signature sets
-
 15:09
15:09
f5 asm lab 6: user-defined attack signatures
-
 12:24
12:24
big-ip awaf demo 22 - use and enforce attack signatures with f5 big-ip adv waf (formerly asm)
-
 12:21
12:21
f5-bigip asm - module 7 attack signature (part2 ) #f5asm #attacksignature #waf
-
 2:18
2:18
2 minute tech tip: asm attack signature update
-
 9:48
9:48
big-ip awaf demo 27 - use custom attack signatures with f5 big-ip adv waf (formerly asm)
-
 1:28
1:28
mitigating app threats and security complexity with big-ip next waf
-
 12:36
12:36
f5 waf - threat landscape ( part 2 of 3 )
-
 19:12
19:12
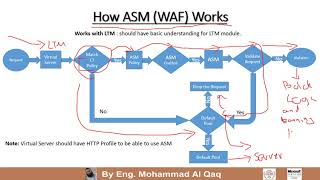
f5 asm application security manager waf by eng mohammad al qaq arabic
-
 11:21
11:21
big-ip awaf demo 47 - block credential stuffing attacks w/ f5 big-ip adv waf (formerly asm)
-
 12:07
12:07
bot management with f5's advanced waf
-
 24:50
24:50
f5 3-day big-ip asm / awaf course - lesson 5 - attack signatures
-
 53:52
53:52
protection from latest network and application attacks
-
 0:57
0:57
the pros and cons of cybersecurity!
-
 13:23
13:23
lecture: 1 || introduction to the f5 advanced waf or f5 asm || f5 waf / asm training - english
-
 58:44
58:44
f5 advance waf training | big-ip asm tutorials| sql injection and brute force protection mitigation
-
 54:58
54:58
f5 big-ip adv waf (asm) vulnerability mitigation | security policy deployment | introduction part-1