give passwords the finger...again! | ssh communications security
Published 1 year ago • 177 plays • Length 0:23Download video MP4
Download video MP3
Similar videos
-
 0:32
0:32
give mfa the finger | ssh communications security
-
![crack ssh private key passwords with john the ripper [tutorial]](https://i.ytimg.com/vi/yhC5Kh5Z_4o/mqdefault.jpg) 12:51
12:51
crack ssh private key passwords with john the ripper [tutorial]
-
 13:09
13:09
why are you better without passwords and keys? | suvi lampila & miikka sainio
-
 32:21
32:21
ssh ukm june 2012 webinar
-
 17:15
17:15
how hackers could brute-force ssh credentials to gain access to servers
-
 3:53
3:53
how ssh password-less key based authentication work in 4 minutes (with example)
-
![hunt down social media accounts by usernames using sherlock [tutorial]](https://i.ytimg.com/vi/HrqYGTK8-bo/mqdefault.jpg) 11:44
11:44
hunt down social media accounts by usernames using sherlock [tutorial]
-
![haunt a computer using ssh [tutorial]](https://i.ytimg.com/vi/M0eEwqUpKDc/mqdefault.jpg) 19:10
19:10
haunt a computer using ssh [tutorial]
-
 7:58
7:58
how to exploit port 80 http on kali linux
-
 4:46
4:46
how to setup password less authentication (ssh,sftp & scp) in linux
-
 10:43
10:43
school of basics | what is ssh | how ssh works
-
 5:43
5:43
how ssh works: secure remote access, file transfers, and tunneling
-
 16:19
16:19
how do i create and use public keys with ssh?
-
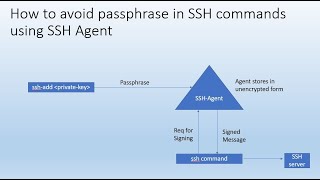 5:44
5:44
how to avoid passphrase in ssh commands using ssh agent
-
 9:20
9:20
how secure shell works (ssh) - computerphile
-
 8:02
8:02
configuring passwordless server login using ssh
-
 24:13
24:13
ssh and scp using key or password less authentication
-
 16:36
16:36
learn object pascal by programming an adventure game. start today!
-
 4:32
4:32
how to: crack an ssh password
-
 52:04
52:04
manage secure shell (ssh) access with time-bound certificates
-
 1:36
1:36
get keycard access to the elevator | alan wake 2 dlc (the lake house)
-
 42:02
42:02
pam without passwords fast tracking 2020 compliance regimes without add ons