how does deception technology work in ot cybersecurity?
Published 2 years ago • 388 plays • Length 3:03Download video MP4
Download video MP3
Similar videos
-
 17:09
17:09
deception technology for industrial cybersecurity environments
-
 28:35
28:35
deceive by design: how to protect critical infrastructure with deception technology
-
 14:40
14:40
transform cyber - the research behind deception technology
-
 52:12
52:12
implementer’s guide to deception technologies
-
 2:23
2:23
what is deception technology and who is cybertrap?
-
 1:21
1:21
what's the real difference between cyber deception and honeypots? | countercraft blog
-
 6:14
6:14
understanding deception technology in cybersecurity | #networkershome
-
 45:21
45:21
expert talk: software security • jim manico & john steven • goto 2022
-
 57:00
57:00
getting started in ics/ot cyber security - 20 hours - part 1 (course introduction)
-
 36:19
36:19
building a secure ot network | sans ics concepts
-
 1:00:34
1:00:34
real world implementation of deception technologies
-
 2:24
2:24
intro to deception technology and attivo networks
-
 15:30
15:30
deception cyber security training & tutorial | top deception tools | soc siem soar edr
-
 2:20
2:20
introduction to ot cybersecurity
-
 1:03:17
1:03:17
how remote connectivity is remaking cybersecurity & industrial operations - transform 2021
-
 4:55
4:55
top 10 deception technology software options
-
![[the lost bots] episode 4: deception technology](https://i.ytimg.com/vi/x90f4Hn3R-Q/mqdefault.jpg) 9:56
9:56
[the lost bots] episode 4: deception technology
-
 11:20
11:20
introduction to ics/ot cybersecurity
-
 1:38:23
1:38:23
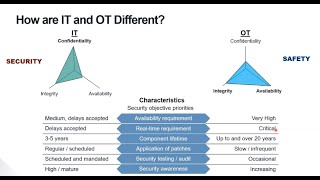
what is ot | what are ot cyber security challenges | ot security solutions | what is ics and scada
-
 1:05:01
1:05:01
l-dih talks - episode 3: cybersecurity in ot vs it, same challenges?
-
 26:29
26:29
leading expert on the use of deception technologies in cybersecurity tony cole