how should mfa be enforced? #cybersecurity #infosec #podcast #news #infosecawareness
Published 4 weeks ago • 1.4K plays • Length 0:30Download video MP4
Download video MP3
Similar videos
-
 0:33
0:33
mfa bombing targets apple users #infosecnews #cybersecurity #podcastclips #apple #compromised
-
 9:05
9:05
an overview of multi-factor authentication and why you need it.
-
 42:01
42:01
threats from the wild - episode 3: multi-factor authentication (mfa) bypass 101
-
 0:15
0:15
get cyber safe challenge 2021 - step 6 - turn on multi-factor authentication
-
 40:46
40:46
from strong to stronger: phishing resistant authentication methods (the blueprint | brk244
-
 17:42
17:42
how security keys work (2fa explained!)
-
 9:22
9:22
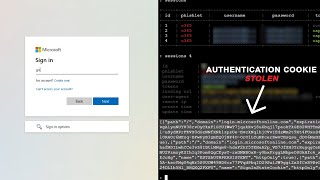
mfa can be easily bypassed - here's how
-
 2:51
2:51
what is mfa or multi-factor authentication?
-
 5:20
5:20
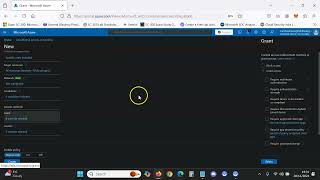
how to set up mfa in microsoft entra conditional access
-
 1:28:10
1:28:10
bhis | how to detect and respond to business email (m365) compromise w/ the bhis dfir team | 1-hour
-
 2:21
2:21
multifactor authentication (mfa): crash course
-
 12:58
12:58
why mfa won't protect you from hackers (and what you can do about it)
-
 3:21
3:21
protect your users from mfa fatigue
-
 2:43
2:43
2023 cybersecurity awareness month: episode 3 — stop tailgating!
-
 3:35
3:35
security risks for boards. are you asking the right questions? - with matt fehon am
-
 1:02:09
1:02:09
the pro’s guide to ibm i security fundamentals
-
 59:39
59:39
the rise of phishing-resistant mfa: how we got here and how to move forward
-
 0:46
0:46
🌐 why should you enable mfa everywhere? 🌐
-
 7:58
7:58
tech tip 1: mfa
-
 21:08
21:08
5. multi-factor authentication and phishing explained - zero trust authentication master class
-
 3:00
3:00
attacker in the endpoint - how mfa is bypassed