asymmetric encryption - simply explained
Published 7 years ago • 1.3M plays • Length 4:40Download video MP4
Download video MP3
Similar videos
-
 11:01
11:01
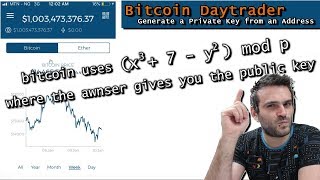
how to generate a private key from a bitcoin watch only address
-
 1:20
1:20
how to convert an ssh2 public key into openssh
-
 12:33
12:33
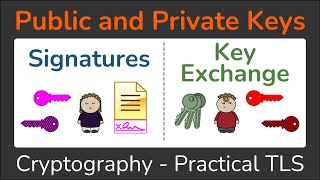
public and private keys - signatures & key exchanges - cryptography - practical tls
-
 3:49
3:49
understand passkeys in 4 minutes
-
 0:34
0:34
hacking into android in 32 seconds | hid attack | metasploit | pin brute force poc
-
 9:43
9:43
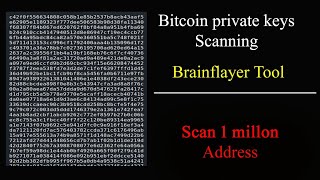
bitcoin private keys cracking | brainflayer guide | convert bitcoin address to hash160
-
 3:52
3:52
boot failure press any key to continue - how to fixed
-
 8:40
8:40
secret key exchange (diffie-hellman) - computerphile
-
 15:46
15:46
how does public key cryptography work – gary explains
-
 4:59
4:59
generate public private key in windows 10 using openssl
-
 4:56
4:56
how to find a private key of (b.t.c) using a bloom filter
-
 5:32
5:32
how to disable dmverity or android verified boot (avb)
-
 3:50
3:50
how to use miracle box to flash feature or basic mtk phones
-
 38:56
38:56
public key cryptography involves a pair of keys known as a public key and a private key.
-
 0:39
0:39
break rsa encryption in 10 lines of python code | #shorts quantum computing with shor's algorithm
-
 0:48
0:48
how to use your smartphone as a door card
-
 3:20
3:20
phone as a key
-
 0:40
0:40
importing private key with mycelium app
-
![mac stuck at update, apple logo, loading screen, startup [fixed] - no internet required [easy fast](https://i.ytimg.com/vi/TIFAE-Lk0V4/mqdefault.jpg) 6:03
6:03
mac stuck at update, apple logo, loading screen, startup [fixed] - no internet required [easy fast
-
 8:15
8:15
turn an old pc into an android pc | how to install android os on a laptop or desktop pc
-
 1:35
1:35
whosgamingnow | how to get a free steam key
-
 3:21
3:21
vpc follow along - nat