identification and aaa - cybersecurity roles, processes & operating system security
Published 4 years ago • 16 plays • Length 7:53
Download video MP4
Download video MP3
Similar videos
-
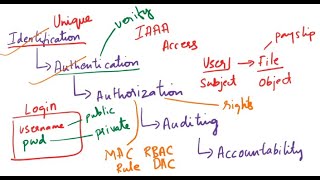 9:56
9:56
what is identification, authentication, authorization, auditing, accountability| iaaa| cybersecurity
-
 9:04
9:04
authentication, authorization, and accounting - comptia security sy0-701 - 1.2
-
 2:37
2:37
what is identification, authentication, authorization? | iaa | cybersecurity
-
 2:26
2:26
aaa framework explained: authentication, authorization, accouting (cybersecurity)
-
 4:32
4:32
oauth 2 explained in simple terms
-
 5:50
5:50
aaa framework and radius
-
 4:34
4:34
what is aaa (authentication, authorisation, & accounting) & iam? - beginner's cyber security series
-
 6:51
6:51
cybersecurity threat hunting explained
-
 8:04
8:04
understanding identification, authorization and authentication | free cyber work applied series
-
 9:11
9:11
what is iam? | identity and access management for beginners (iam) | iam for beginners | simplilearn
-
 0:38
0:38
roles and identity access management
-
 3:37
3:37
identity & access management (iam)
-
 0:53
0:53
what is identity and access management? iam explained
Clip.africa.com - Privacy-policy
 9:56
9:56
 9:04
9:04
 2:37
2:37
 2:26
2:26
 4:32
4:32
 5:50
5:50
 4:34
4:34
 6:51
6:51
 8:04
8:04
 9:11
9:11
 0:38
0:38
 3:37
3:37
 0:53
0:53