identity and access management - the key to a successful zero trust model
Published 4 years ago • 250 plays • Length 2:31Download video MP4
Download video MP3
Similar videos
-
 3:43
3:43
zero trust explained in 4 mins
-
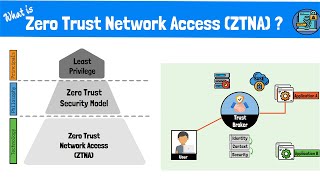 7:44
7:44
what is zero trust network access (ztna)? the zero trust model, framework and technologies explained
-
 47:22
47:22
identity: the key to zero trust security
-
 2:20
2:20
protect your supply chain with identity access management and zero trust
-
 36:36
36:36
zero trust foundations - identity & access management
-
 10:58
10:58
when jtoh towers want to be tofaf - jtoh descending project
-
 10:11
10:11
what is middleware?
-
 7:38
7:38
zero trust security (zts) explained: a beginner's guide for 2024
-
 1:02:52
1:02:52
identity-driven security: the key to zero trust
-
 18:11
18:11
zero trust overview (part 1)
-
 4:30
4:30
how a major financial institution strengthens network security | customer stories
-
 17:59
17:59
cybersecurity and zero trust
-
 2:30
2:30
healthfirst applies an identity security first approach to implement zero trust | cyberark
-
 8:00
8:00
understanding the 7 keys to zero trust authentication
-
 41:54
41:54
delivering a zero trust strategy built on effective identity & access management | ibm
-
 3:37
3:37
identity & access management (iam)
-
 5:06
5:06
zero trust authentication defined
-
 14:39
14:39
29. the journey to zero trust starts with authentication
-
 1:04:36
1:04:36
the journey to zero trust: start with privilege protection & identity security
-
 2:20
2:20
identity and access management with guidehouse’s amanda kane
-
 9:11
9:11
what is iam? | identity and access management for beginners (iam) | iam for beginners | simplilearn
-
 36:28
36:28
secure user identities to establish zero trust