what is a cryptographic hashing function? (example purpose)
Published 3 years ago • 94K plays • Length 7:08Download video MP4
Download video MP3
Similar videos
-
 20:23
20:23
optimal security proofs for full domain hash, revisited.
-
 9:45
9:45
what is hashing? | what is hashing with example | hashing explained simply | simplilearn
-
 10:46
10:46
usenix security '21 - poseidon: a new hash function for zero-knowledge proof systems
-
 0:52
0:52
proofs of work - applied cryptography
-
 8:12
8:12
hashing algorithms and security - computerphile
-
 2:50
2:50
what actually is a hash function?
-
 13:52
13:52
static sift tutorial - tribolelectrostatic separation of trichome heads
-
 5:06
5:06
how secure is 256 bit security?
-
 18:39
18:39
python hash sets explained & demonstrated - computerphile
-
 7:28
7:28
passwords & hash functions (simply explained)
-
 5:55
5:55
what the hash? - how bitcoin and blockchains use hash functions
-
 12:58
12:58
hashrates, target and difficulty in proof of work mining
-
 10:59
10:59
hashing explained
-
 20:04
20:04
comp6441 : hashes, preimage and collision resistance
-
 13:56
13:56
hash tables and hash functions
-
 23:40
23:40
basics of hash analysis and security testing | tryhackme crackthehash
-
 0:58
0:58
what is salting and hashing? #techexplained #tech
-
 7:55
7:55
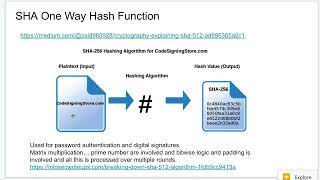
one way hash explained
-
 4:29
4:29
how hash function work?
-
 39:40
39:40
lecture 14: non-sha256 proof-of-work
-
 3:52
3:52
hash tables in 4 minutes
-
 0:50
0:50
hashing, explained in 50 seconds