secure trusted overlay networks for robust privacy-protecting communication
Published 8 years ago • 56 plays • Length 48:09Download video MP4
Download video MP3
Similar videos
-
 14:13
14:13
what are the benefits of using overlay networks?
-
 4:09
4:09
identity protection for workplace from facebook using azure active directory
-
 21:42
21:42
designing scalable networks for large ai clusters: challenges and key insights | jithin jose
-
 16:15
16:15
9 signs your phone has been tapped & what you need to do
-
 6:34
6:34
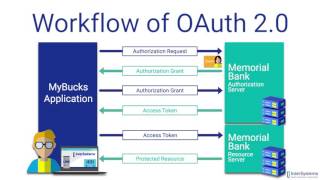
oauth 2.0: an overview
-
 9:01
9:01
virtual networks in microsoft azure
-
 10:46
10:46
microsoft entra private access & risk based policies
-
 1:12:20
1:12:20
privacy-protecting technologies for collaborative research
-
 1:29
1:29
overlay networks in general - georgia tech - advanced operating systems
-
 4:37
4:37
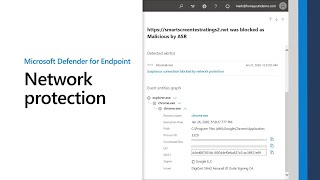
network protection in microsoft defender for endpoint
-
 7:22
7:22
data security: protect your critical data (or else)
-
 1:02
1:02
secure purdue: privacy on social networks
-
 37:56
37:56
srecon17 americas - zero trust networks: building trusted systems in untrusted networks
-
 0:17
0:17
microsoft's identity overlay network (ion)