threat log overview | product demo
Published 2 years ago • 1K plays • Length 2:16Download video MP4
Download video MP3
Similar videos
-
 2:44
2:44
abnormal inbound email protection overview | product demo
-
 1:43
1:43
abuse mailbox overview | product demo
-
 2:44
2:44
abnormal account takeover protection (ato) overview | product demo
-
 1:59
1:59
use case: malware - link
-
 12:27
12:27
abnormal @ rsac: the next chapter of email security is here
-
 2:23
2:23
use case: lateral phishing
-
 4:31
4:31
how do automatic block signals work? | axle counter | block and interlocking system
-
 17:15
17:15
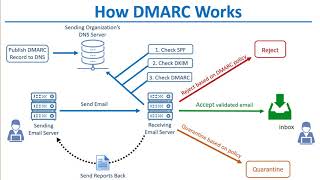
how dkim spf & dmarc work to prevent email spoofing
-
 30:09
30:09
threat hunting interview questions and answers | cybersecurity interview | threat hunting
-
 2:51
2:51
crowdstrike abnormal: integration demo
-
 2:05
2:05
get your cloud email protected in seconds | api integration demo
-
 12:46
12:46
securonix demo
-
 3:46
3:46
abnormal security ceo on threat detection
-
 2:02
2:02
secure your cloud email with abnormal
-
 4:20
4:20
how abnormal uses ai to stop generative ai attacks
-
 10:15
10:15
rsac 2024: abnormal intros unified account takeover protection
-
 2:08
2:08
the evolution of email security | abnormal security
-
 1:22
1:22
an abnormal approach to email security
-
 6:51
6:51
cybersecurity threat hunting explained