usenix enigma 2016 - what makes software exploitation hard?
Published 8 years ago • 6.6K plays • Length 21:43Download video MP4
Download video MP3
Similar videos
-
 20:37
20:37
usenix enigma 2016 - trust beyond the first hop–what really happens to data sent to https websites
-
 20:57
20:57
usenix enigma 2016 - why is usable security hard, and what should we do about it?
-
 20:11
20:11
usenix enigma 2016 - tostatichtml for everyone! about dompurify, ...
-
 21:28
21:28
usenix enigma 2019 - how to predict which vulnerabilities will be exploited
-
 20:47
20:47
usenix enigma 2016 - usable security–the source awakens
-
 21:28
21:28
usenix enigma 2019 - how to predict which vulnerabilities will be exploited
-
 19:05
19:05
usenix enigma 2023 - invited talk: metric perversity and bad decision-making
-
 6:52
6:52
meet the 26-year-old hacker who built a self-driving car... in his garage
-
 5:50
5:50
software licensing is easy with enigma protector!
-
 34:56
34:56
usenix enigma 2016 - nsa tao chief on disrupting nation state hackers
-
 20:45
20:45
usenix enigma 2016 - building a competitive hacking team
-
 19:52
19:52
usenix enigma 2016 - timeless debugging
-
 21:08
21:08
usenix enigma 2017 — hacking sensors
-
 17:41
17:41
usenix enigma 2016 - from concept to deployment - the life (and death) of security features
-
 19:56
19:56
usenix enigma 2016 - the golden age of bulk surveillance
-
 18:38
18:38
usenix enigma 2016 - a million hit points and infinite charisma: how games can fix...
-
 21:15
21:15
usenix enigma 2016 - hacking health: security in healthcare it systems
-
 22:34
22:34
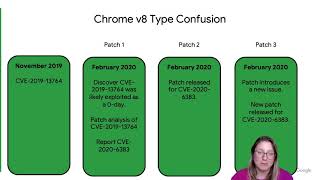
usenix enigma 2021 - the state of 0-day in-the-wild exploitation
-
 26:04
26:04
usenix enigma 2016 - defending, detecting, and responding to hardware and firmware attacks
-
 26:00
26:00
usenix enigma 2016 - lessons learned while protecting gmail