using zero trust to prepare for data breaches.
Published 1 year ago • 86 plays • Length 1:00Download video MP4
Download video MP3
Similar videos
-
 3:43
3:43
zero trust explained in 4 mins
-
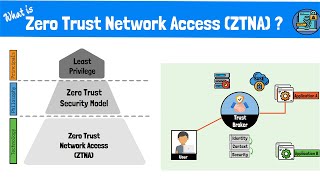 7:44
7:44
what is zero trust network access (ztna)? the zero trust model, framework and technologies explained
-
 57:54
57:54
new ways to take control over data privacy with kurt long.
-
 38:52
38:52
zero trust. new approaches to understanding social engineering.
-
 41:00
41:00
how to plan for ransomware
-
 38:27
38:27
ransomware. how to get your data back
-
 10:21
10:21
zero trust cybersecurity explained
-
 21:46
21:46
zero trust explained | real world example
-
 45:10
45:10
zero trust data security explained
-
 0:58
0:58
what is zero trust? learn application security
-
 2:51
2:51
data security and protection with zero trust
-
 0:59
0:59
new nsa guide on ransomware
-
 5:03
5:03
zero trust - principles to safeguard your data
-
 0:56
0:56
zero trust explained
-
 20:00
20:00
understanding zero trust security
-
 0:13
0:13
what is zero trust architecture?
-
 0:41
0:41
seqrite hawkkprotect – zero-trust user access
-
 4:38
4:38
how zero trust security works
-
 0:59
0:59
zero trust and cybersecurity