what is the cyber kill chain?
Published 6 years ago • 4.6K plays • Length 1:04Download video MP4
Download video MP3
Similar videos
-
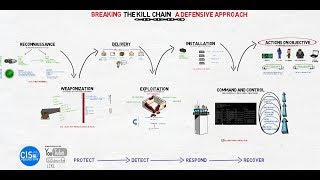 13:18
13:18
breaking the kill chain: a defensive approach
-
 6:44
6:44
the cyber kill chain
-
 1:34
1:34
what is the cyber kill chain? | webinar excerpt
-
 2:05
2:05
cyber kill chain: what it is, how it works
-
 11:35
11:35
the cyber kill chain | how hackers do what they do
-
 7:31
7:31
what is cyber kill chain # the 7 steps of a cyberattack
-
 2:40
2:40
the cyber kill chain explained with real examples (2024)
-
 4:53
4:53
understanding cyber kill chain | ethical hacking | eduonix
-

naval invasion in lebanon, huge russian losses! breaking war news with the enforcer (983)
-
 1:01:37
1:01:37
the kill chain: defending america in the future of high-tech warfare
-
![comptia cysa - complete course with labs [10 hours]](https://i.ytimg.com/vi/kFfAr6wRp7M/mqdefault.jpg) 10:10:47
10:10:47
comptia cysa - complete course with labs [10 hours]
-
 4:42
4:42
learn the basics of the cyber kill chain
-
 14:55
14:55
real hacking: learn the cyber kill chain
-
 13:39
13:39
cyber kill chain | cyber kill chain explain | what is cyber kill chain? kill chain | cybersecurity
-
 13:55
13:55
the cyber kill chain and how to identify indicators of compromise
-
 57:58
57:58
cyber kill chain: the anatomy of a cyber attack
-
 3:55
3:55
understanding the cyber security kill chain
-
 3:51
3:51
lockheed martin's cyber kill chain
-
 1:43
1:43
cyber kill chain explained
-
 2:03
2:03
what is cyber kill chain? | all 7 steps explained
-
 3:44
3:44
cydef and the cyber kill chain
-
 5:32
5:32
lockheed martin cyber kill chain | the defender's mini playbook