zero trust security model explained (how to apply zero trust)
Published 2 years ago • 238 plays • Length 6:57Download video MP4
Download video MP3
Similar videos
-
 3:43
3:43
zero trust explained in 4 mins
-
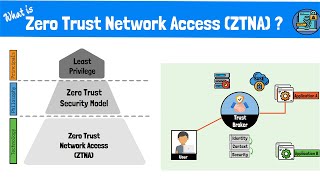 7:44
7:44
what is zero trust network access (ztna)? the zero trust model, framework and technologies explained
-
 7:28
7:28
zero trust explained in 7 minutes
-
 17:59
17:59
cybersecurity and zero trust
-
 12:25
12:25
🔥zero trust security model explained simply | what is zero trust security?
-
 4:38
4:38
how zero trust security works
-
 2:17
2:17
proxy interview i busted fake interview. girl was unable to speek at end😂😂
-
 7:38
7:38
zero trust security (zts) explained: a beginner's guide for 2024
-
 10:31
10:31
ultimate guide to zero trust for businesses
-
 5:27
5:27
zero trust security model explained
-
 2:12
2:12
zero trust explained
-
 0:58
0:58
what is zero trust? learn application security
-
 21:46
21:46
zero trust explained | real world example
-
 30:42
30:42
zero trust security architecture with microsoft mvp - webinar
-
 45:42
45:42
overview of zero trust architectures
-
 9:25
9:25
zero trust architecture explained | shield classroom | manageengine
-
 39:26
39:26
how to approach a zero trust security model
-
 2:31
2:31
what is zero trust security?
-
 8:57
8:57
zero trust security implementation - essentials series - episode 1
-
 0:51
0:51
why zero trust is a controversial cybersecurity debate
-
 57:11
57:11
understanding and getting started with zero trust
-
 37:45
37:45
implementing zero trust architecture: a step-by-step guide part 1