zero trust series, part 3: how to implement zero trust identity architecture
Published 1 year ago • 38 plays • Length 2:54Download video MP4
Download video MP3
Similar videos
-
 3:43
3:43
zero trust explained in 4 mins
-
 4:59
4:59
zero trust – your 3 step introduction guide.
-
 1:02:06
1:02:06
zero trust implementation: a how to guide
-
 7:44
7:44
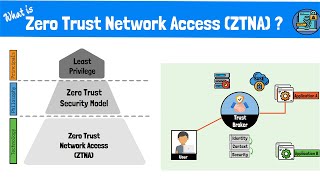
what is zero trust network access (ztna)? the zero trust model, framework and technologies explained
-
 12:50
12:50
implementing zero trust
-
 38:21
38:21
zero trust (tic 3.0) solution
-
 37:45
37:45
implementing zero trust architecture: a step-by-step guide part 1
-
 51:54
51:54
what we learned implementing zero trust security at microsoft
-
 10:28
10:28
zero trust authentication and architecture within nist 800-207 framework
-
 18:11
18:11
zero trust overview (part 1)
-
 5:26
5:26
zscaler zero trust exchange explained | 5-min overview
-
 21:46
21:46
zero trust explained | real world example
-
 26:37
26:37
episode 03: zero trust
-
 0:15
0:15
growing up pentecostal... #short
-
 9:58
9:58
zero trust for endpoints and applications - essentials series - episode 3
-
 0:21
0:21
imagine dating millionaire girl! 😍 dm for miami yacht rentals 🛥️ #miamipromoters #miamiboatrentals
-
 0:15
0:15
did i marry him for the money? prenup? #shorts
-
 0:14
0:14
finding girlfriend in philippines (in 10sec) 😏
-
 6:57
6:57
why implement zero trust
-
 32:47
32:47
cybersecurity zero trust architecture : explained for beginners
-
 0:58
0:58
what is zero trust? learn application security