deanonymizing double spenders solution - applied cryptography
Published 12 years ago • 475 plays • Length 0:21Download video MP4
Download video MP3
Similar videos
-
 0:23
0:23
deanonymizing double spenders - applied cryptography
-
 0:36
0:36
double hash solution - applied cryptography
-
 2:53
2:53
eavesdropper solution - applied cryptography
-
 0:25
0:25
salted password scheme solution - applied cryptography
-
 1:23:48
1:23:48
perpetual encryption with yevgeniy dodis | a16z research
-
 8:34
8:34
was your vote counted? (feat. homomorphic encryption) - numberphile
-
 1:29:39
1:29:39
lecture 3: stream ciphers, random numbers and the one time pad by christof paar
-
 0:44
0:44
wire labels solution - applied cryptography
-
 1:12
1:12
eke authentication implementation solution - applied cryptography
-
 0:31
0:31
secure computation solution - applied cryptography
-
 1:32
1:32
pairwise distribution solution - applied cryptography
-
 1:35
1:35
tor solution - applied cryptography
-
 0:19
0:19
toy substitution cipher 2 solution - applied cryptography
-
 0:13
0:13
compute e solution - applied cryptography
-
 0:50
0:50
eke authentication solution - applied cryptography
-
 1:26
1:26
basic tls solution - applied cryptography
-
 1:48
1:48
decrpytion in parallel solution - applied cryptography
-
 0:24
0:24
convincing solution - applied cryptography
-
 1:13
1:13
invertibility of rsa solution - applied cryptography
-
 0:56
0:56
auditing tradeoffs solution - applied cryptography
-
 0:30
0:30
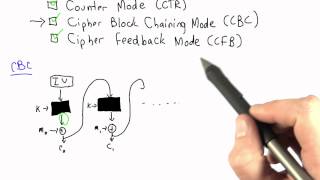
cbc implementation solution - applied cryptography