how do attackers bypass mfa?
Published 1 year ago • 13 plays • Length 1:27Download video MP4
Download video MP3
Similar videos
-
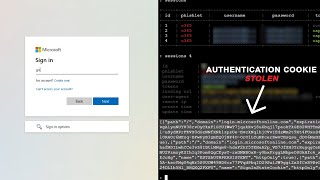 9:22
9:22
mfa can be easily bypassed - here's how
-
 6:28
6:28
how mfa bypass attacks work
-
 10:16
10:16
hacking two factor authentication: four methods for bypassing 2fa and mfa
-
 3:58
3:58
attacker in the middle - how mfa is bypassed
-
 3:55
3:55
mfa fatigue attacks - how mfa is bypassed
-
 5:24
5:24
aitm attack: how to bypass any mfa and the steps you can take to protect your business (en version)
-
 44:07
44:07
how attackers can bypass phishing-resistant mfa | use these protections!
-
 9:20
9:20
how hackers bypass two-factor authentication (2fa)?!
-
 48:22
48:22
bypassing advance root detections using frida
-
 5:38
5:38
microsoft 365 security basics: mfa fraud alert
-
 38:40
38:40
cyber security workshop presented by: silicon plains
-
 25:14
25:14
how hackers bypass mfa! - (multi-factor authentication)
-
 13:40
13:40
mfa bypass via phishing: how attackers exploit weaknesses and what you can do
-
 15:30
15:30
dfsp # 454 mfa bypass attacks
-
 3:11
3:11
0ktapus - how mfa is bypassed
-
 42:01
42:01
threats from the wild - episode 3: multi-factor authentication (mfa) bypass 101
-
 52:55
52:55
mitigating mitm phishing toolkit attacks that bypass mfa
-
 15:31
15:31
dfsp # 454 mfa bypass attacks
-
 0:58
0:58
how to prevent attacks that bypass mfa
-
 3:00
3:00
attacker in the endpoint - how mfa is bypassed
-
 4:18
4:18
how criminals bypass multi-factor authentication (mfa)